Памяти и накопители Seagate (ST16000NM002G) - инструкция пользователя по применению, эксплуатации и установке на русском языке. Мы надеемся, она поможет вам решить возникшие у вас вопросы при эксплуатации техники.
Если остались вопросы, задайте их в комментариях после инструкции.
"Загружаем инструкцию", означает, что нужно подождать пока файл загрузится и можно будет его читать онлайн. Некоторые инструкции очень большие и время их появления зависит от вашей скорости интернета.

Seagate Exos X16 SAS Product Manual, Rev. K
34
www.seagate.com
About FIPS
7.0
About FIPS
The Federal Information Processing Standard (FIPS) Publication 140-2 is a U.S. Government Computer Security Standard used to accredit
cryptographic modules. It is titled 'Security Requirements for Cryptographic Modules (FIPS PUB 140-2)' and is issued by the National Institute of
Standards and Technology (NIST ).
Purpose
This standard specifies the security requirements that will be satisfied by a cryptographic module utilized within a security system protecting
sensitive but unclassified information. The standard provides four increasing, qualitative levels of security: Level 1, Level 2, Level 3 and Level 4.
These levels are intended to cover the wide range of potential applications and environments in which cryptographic modules may be employed.
Validation Program
Products that claim conformance to this standard are validated by the Cryptographic Module Validation Program (CMVP) which is a joint effort
between National Institute of Standards and Technology (NIST ) and the Communications Security Establishment (CSE) of the Government of
Canada. Products validated as conforming to FIPS 140-2 are accepted by the Federal agencies of both countries for the protection of sensitive
information (United States) or Designated Information (Canada).
In the CMVP, vendors of cryptographic modules use independent, accredited testing laboratories to have their modules tested. National Voluntary
Laboratory Accreditation Program (NVLAP) accredited laboratories perform cryptographic module compliance/conformance testing.
Seagate Enterprise SED
visit - http://csrc.nist.gov/groups/STM/cmvp/documents/140-1/1401vend.htm, and search for “Seagate”.
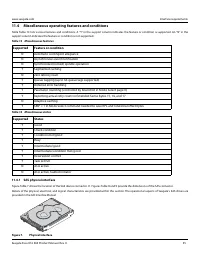
Security Level 2
Security Level 2 enhances the physical security mechanisms of a Security Level 1 cryptographic module by adding the requirement for tamper-
evidence, which includes the use of tamper-evident coatings or seals on removable covers of the module. Tamper-evident coatings or seals are
placed on a cryptographic module so that the coating or seal must be broken to attain physical access to the critical security parameters (CSP)
within the module. Tamper-evident seals (example shown in
) are placed on covers to protect against unauthorized physical access. In addi-
tion Security Level 2 requires, at a minimum, role-based authentication in which a cryptographic module authenticates the authorization of an
operator to assume a specific role and perform a corresponding set of services
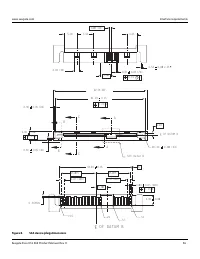
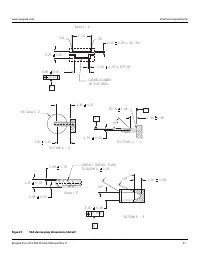
Figure 4. Example of FIPS tamper evidence labels.
Note
Image is for reference only, may not represent actual drive.
Характеристики
Остались вопросы?Не нашли свой ответ в руководстве или возникли другие проблемы? Задайте свой вопрос в форме ниже с подробным описанием вашей ситуации, чтобы другие люди и специалисты смогли дать на него ответ. Если вы знаете как решить проблему другого человека, пожалуйста, подскажите ему :)